Identify breaches fast through real time expert analysis of your environments by experts
Why you need it
Securing your perimeter is a must. However, you should assume that things will get through, or already be inside. When this happens, you need to quickly identify those threats and attacks. This takes a combination of technology and expertise.
Claranet’s service provides Threat Detection and 24/7 monitoring capabilities, providing real-time analysis of the security alerts that are generated by your applications, network devices, hardware, and end points on your network. Our experts validate these alerts and quickly inform you to any breaches or risks.
We add new experts to your team
In an area where speed is vital, our dedicated Security Operations Centre team work as an extension of your business, saving you time, money, and customer reputation. Any Security Information and Event Management (SIEM) tool will generate large quantities of alerts, many of them false positives. They all need to be reviewed, qualified, and prioritised by an experienced eye. This takes time and resources. Our experience and support in this area has proved to be invaluable to our customers' IT response times.
Monitoring and predicting threats around the clock, we can remove the resource pressure of research analysis that is required to accurately identify and prioritise the security incidents that are discovered on your network.

Three core elements
Three areas that are essential for an effective defence and detection service:
- Security Information and Event Monitoring software (SIEM)
- Threat Intelligence feeds
- A team of expert security analysts who can alert you, but also advise and discuss the threat with you

What we do
There are a number of stages within the Claranet Managed Detection and Response cycle which ensure that your service is configured correctly and evolves in line with experience:
Identify: Identify all of the assets within your organisation to create an understanding of the management of the cybersecurity risk to your systems, data, assets, and your overall capabilities.
Architect: Scope and design the service to meet your security and corporate goals.
Protect: To monitor all the security events for indicators of compromise.
Response: Build an investigative report that shows what the compromise was and exactly what we found.
Optimise: To continually evolve the system in line with any changes to both internal and external threats.
How it works
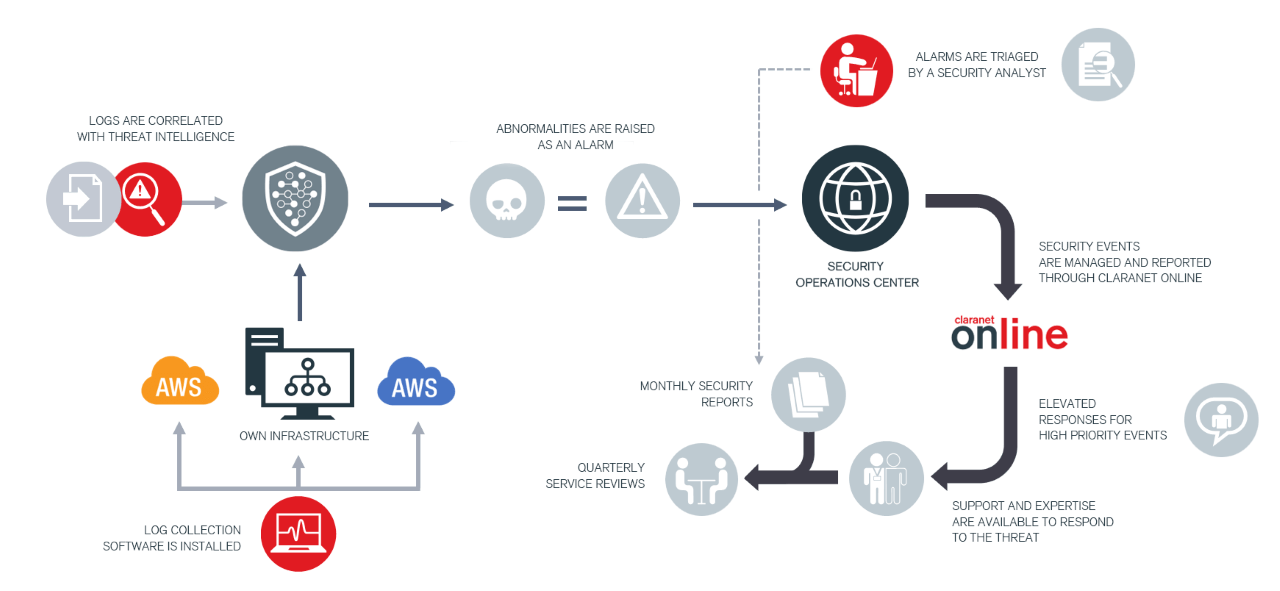

Prevention can be better than cure
Check out our Continuous Security Testing service to gain insight into your vulnerabilities significantly faster than through traditional penetration testing. Find out where your vulnerabilities lie before they can be exploited.
Benefits of a SOC managed by Claranet Cyber Security
Manage costs better
Removes the need for a large CAPEX investment for an in-house SOC
Remove distractions
Removes the on-going cost of security recruitment and retention
Tailored to your needs
Provides a SIEM tailored to your network by our expert SOC engineers
Improve your response
Increases efficiency of incident handling and IT compliance
Proactive security management
Includes threat hunting, intelligence gathering, and malware analysis
Streamline compliance reporting
Centralises log collection, analysis, and retention
Our accreditations





